A critical vulnerability has been discovered in AutoGPT, an open-source program that uses GPT-3 to automate various tasks. This vulnerability, assigned CVE-2024-1879, is a severe Cross-Site Request Forgery (CSRF) issue that affects version 0.5.0 of the product. The flaw allows attackers to execute arbitrary commands on the AutoGPT server by exploiting weaknesses in the API endpoint, which lacks adequate protection mechanisms.
The vulnerability comes from insufficient CSRF defense mechanisms on the API endpoint responsible for processing instructions in AutoGPT. Attackers manipulate authenticated users into performing unintended actions by making unauthorized requests to a web application where they are authenticated in CSFR.
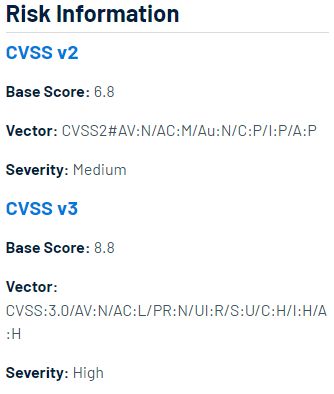
Here’s how the vulnerability can be exploited:
- Initially, an attacker sets up a malicious website designed to send crafted requests to the AutoGPT server.
- The user, running AutoGPT within their local network, visits the malicious website.
- The malicious site sends specially crafted requests to the AutoGPT API endpoint.
- Due to the lack of CSRF protections, the AutoGPT server accepts and processes these requests, leading to arbitrary command execution.
The situation is further complicated by AutoGPT’s default Cross-Origin Resource Sharing (CORS) configuration, which allows requests from any origin. Moreover, this permissive setting enables attackers to read responses from cross-site requests, significantly increasing the potential impact of the vulnerability.
Successful exploitation of CVE-2024-1879 can lead to severe consequences, including unauthorized command execution on the server, potential data theft, and compromise of the system’s integrity and confidentiality.
Fortunately, this vulnerability has been addressed in AutoGPT version 5.1. The patch includes robust CSRF protections on the API endpoints and restrictions on CORS policies to allow only trusted origins.
For cybersecurity specialists and system administrators using AutoGPT, it is imperative to take the following actions:
- Firstly, update to AutoGPT version 5.1 or later to ensure the vulnerability is patched.
- Furthermore, regularly review and tighten CORS policies and other security configurations.
- Additionally, implement monitoring solutions to detect unusual traffic patterns that may indicate exploitation attempts.
The vulnerability in this open-source platform is a timely reminder of the significance of strong security procedures in software development. Organizations can protect themselves from such attacks by understanding the technical details of this vulnerability and deploying the necessary updates and configurations.