According to Microsoft, state-sponsored APT groups with ties to North Korea have started leveraging artificial intelligence (AI) to improve the effectiveness and efficiency of their operations, leading to a rise of AI-Powered Cyberattacks.
What is an APT Group?
An APT (Advanced Persistent Threat) group is a highly proficient and well-organized group of cyber attackers. This group of cyber attackers carries out continuous sophisticated cyberattacks on a specific target. They usually have particular goals like espionage or sabotage. They typically have support from a nation-state or other well-funded enterprise.
Who are the North Korean APT Group?
North Korean hackers are usually associated with the country’s government agencies, and they are known to operate under various names and groups. One of the most famous North Korean APT Groups is the Lazarus Group. The Lazarus group goes by several names like Hidden Cobra, Guardians of Peace, or APT38.
Several high-profile cyber attacks have been linked to the Lazarus APT group, including the 2014 Sony Pictures hack and the 2017 WannaCry ransomware attack.
The Emerald Sleet APT Group
The North Korean in focus for this article is the Emerald Sleet APT Group, which is also known as Kimusky.
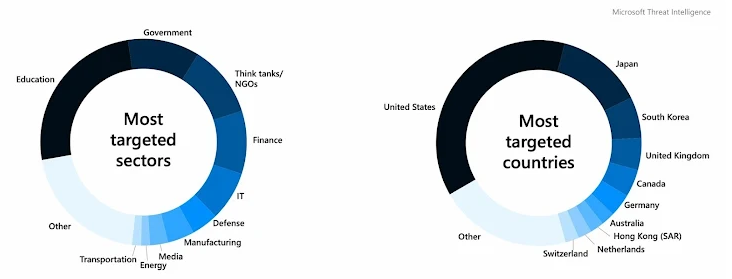
This North Korean APT group mainly goes after governments, think tanks and other entities involved with the Korean Peninsula. Lately, they’ve also been aiming for locations in the UN, Europe, Russia, and the United States. They gather info about foreign policy, security, nuclear programs, and sanctions on North Korea.
How is the Emerald Sleet APT Group leveraging AI?
Recent reports say they have been seen leveraging LLMs to support spear-phishing attacks against specialists on the Korean Peninsula.
The Emerald Sleet APT is reported to have joined Chinese hacker crews that are using AI-generated content for influence operations by using the most recent developments in AI to identify vulnerabilities and do reconnaissance on groups and specialists concentrating on North Korea.
According to Redmond, it also used LLMs to write text for spear-phishing emails, detect technical difficulties, and perform simple scripting jobs.
Proofpoint, another firm, also discussed this. They claimed that to initiate contact with their targets, these hackers pose as friendly to gain trust. Afterward, they attempt to obtain classified information.
They pose as representatives of research centers and other organizations to make their emails appear authentic. This enhances the attack’s chances of success.
AI tools, an advantage or a disadvantage?
The National Cyber Security Centre of the United Kingdom recently highlighted the dangers of AI-powered cyberattacks. They also predicted that over the next two years, the development of AI technology will lead to a rise in cyber threats.
Furthermore, in his introduction to the quarterly “Cyber Signals” report, Bret Arsenault of Microsoft emphasized the dual nature of AI tools, bringing both benefits and challenges in cybersecurity.
Conclusion
Although artificial intelligence (AI) strengthens defenses against cyberattacks, hackers also use AI to plan more complex operations. Looking ahead, the evolution of AI in social engineering tactics, potentially enabling deepfakes and voice cloning, poses further challenges.
In light of this, the cybersecurity community needs to work together and take proactive steps to navigate cyberspace and protect against the threat of AI-powered cyberattacks.





