Recently, researchers identified a critical vulnerability, CVE-2024-21552, in the SuperAGI application. This eval function vulnerability is particularly alarming because it enables attackers to execute any code, thus posing a serious threat to affected systems.
CVE-2024-21552 stems from using the eval function in SuperAGI. Although eval serves as a valuable tool for executing code from strings, it poses significant risks due to its ability to run any code provided, including harmful scripts. Specifically, SuperAGI processes outputs from the Language Learning Model (LLM) through eval without adequate checks or sanitization. As a result, attackers can craft specific inputs to exploit eval, thereby executing arbitrary code on the server.
Here’s a simplified example of how the vulnerable code might look:
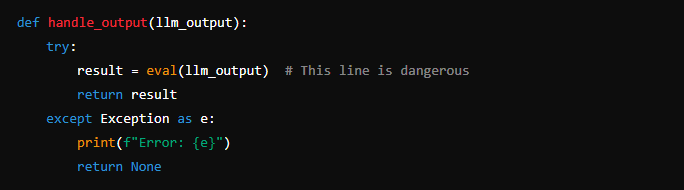
In this example, llm_output is being directly passed to eval, which poses a severe security risk. In this case, on attacker can exploit this to execute arbitrary code on the server.
The impact of this eval function vulnerability is severe. If exploited, attackers could execute any code on the server. This may include commands to steal data, alter configurations, or cause other malicious effects. Consequently, unauthorized access to sensitive information could occur, and the system might experience a denial-of-service (DoS) condition due to malicious requests or commands.
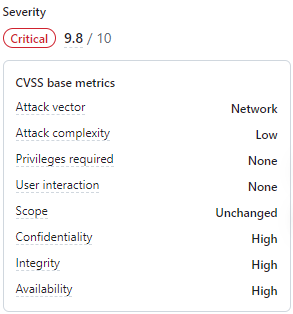
Addressing CVE-2024-21552 requires immediate and robust actions:
- Replace eval with safer alternatives. For example, Python’s
ast.literal_evalcan safely evaluate strings containing Python literals. - Validate and sanitize all inputs to functions like eval. This measure can prevent the execution of malicious code.
- Conduct a comprehensive code review to identify and refactor instances where eval is used. This effort should be part of a broader strategy to eliminate unsafe coding practices.
- Stay up-to-date with software updates and patches. Apply any updates provided by the software vendor to address this vulnerability.
- Finally, educate your development team about the dangers of functions like eval and promote secure coding practices. This approach can help prevent similar vulnerabilities in the future.
In conclusion, CVE-2024-21552 is a critical reminder of the importance of secure coding practices. By understanding the risks associated with functions like eval and implementing strong validation and sanitization measures, developers can significantly mitigate the threat posed by such vulnerabilities. Staying informed and proactive is essential to protecting systems from exploitation.





