A critical vulnerability has been discovered in the EmailGPT service, an API-based tool that automates email generation using AI. This vulnerability, assigned CVE-2024-5184, is a severe prompt injection flaw affecting all versions of the product. The flaw allows attackers to take control of the service logic by injecting malicious prompts, leading to unauthorized data disclosure and potentially harmful operations.
The vulnerability stems from inadequate input validation in the API endpoint responsible for processing prompts in EmailGPT. Attackers can exploit this weakness by sending crafted requests that manipulate the service into performing unintended actions, such as leaking sensitive information or executing arbitrary commands.
This vulnerability can be exploited by:
An attacker with access to the EmailGPT service submits a specially crafted prompt.
The service processes the prompt without proper validation.
The crafted prompt forces the AI to reveal hard-coded system prompts or execute malicious commands.
This results in unauthorized actions or data leaks.
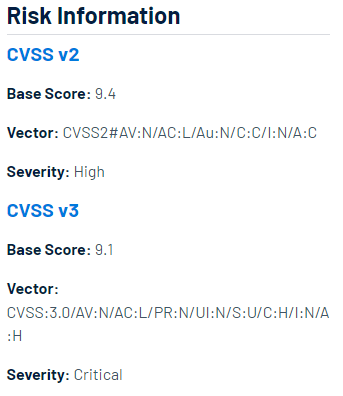
The vulnerability is highly critical, as shown by its CVSS scores. The National Vulnerability Database (NVD) assigns it a CVSS v3.1 base score of 9.1, while Synopsys, the CNA (CVE Numbering Authority) responsible for this record, provides a CVSS v4.0 score of 8.5, highlighting the significant risk it poses to systems using EmailGPT.
For cybersecurity specialists and system administrators using EmailGPT, it is imperative to take the following actions:
- Firstly, update to the latest security patches and versions provided by EmailGPT to mitigate this vulnerability.
- Furthermore, implement robust mechanisms to sanitize and validate all inputs to the API service, preventing the system from processing malicious prompts.
- Restrict access to the EmailGPT service to authorized users only and enforce strict access control policies.
- Enable comprehensive logging and monitoring to detect and respond to any unusual activity or attempts to exploit this vulnerability.
In conclusion, the vulnerability in EmailGPT emphasizes the importance of prioritizing security, particularly in services leveraging AI and machine learning. Prompt injection vulnerabilities can have severe consequences. Organizations must proactively address these security gaps to protect their systems and data. Finally, by understanding the technical details of CVE-2024-5184 and deploying necessary updates and configurations, organizations can safeguard against potential exploits.





