In cybersecurity, vigilance is the name of the game. The recent discovery of a critical vulnerability in the Haystack LLM framework serves as a reminder of how even the most sophisticated tools can carry significant flaws. Let’s dive into what happened, why it matters, and what steps have been taken to ensure such incidents are less likely in the future.
The Use Of Jinja2 Templates
Haystack is an all-in-one framework designed to leverage the capabilities of large language models (LLMs), Transformer models, and vector search. It’s a powerful tool that enables developers to build and deploy AI-powered applications quickly. However, with great power comes great responsibility, and sometimes, great risk. The issue at hand involves Jinja2, a widely-used templating engine in Python known for its flexibility and ease of use.
Jinja2 templates allow developers to embed logic into their HTML, generating dynamic content on the fly. However, this flexibility can also be a security nightmare if not handled correctly. In the case of Haystack, certain components allowed users to create and execute pipelines, utilizing Jinja2 templates along the way. The danger emerged when these templates were used without proper safeguards, opening the door to a potential remote code execution (RCE) vulnerability. In layman’s terms, this means that an attacker could craft a malicious template that, when processed, could run arbitrary code on the server—essentially giving them the keys to the kingdom.
The Fix
The discovery of this vulnerability was a critical security flaw that could have had severe implications. Attackers exploiting this vulnerability could have gained unauthorized access to sensitive data, disrupted services, or even used the compromised systems as a launchpad for further attacks. Recognizing the gravity of the situation, the developers behind Haystack moved swiftly to address the issue.
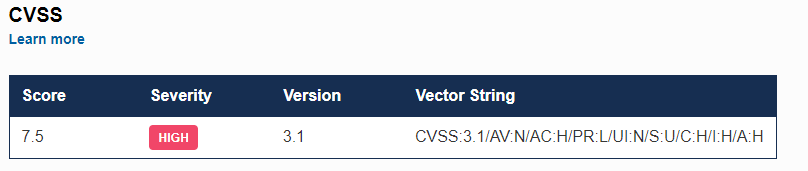
The resolution came in the form of an update—Haystack version 2.3.1. This patch included important changes, particularly around how Jinja2 templates are handled. By implementing stricter controls and ensuring that user inputs are properly sanitized, the developers effectively closed the loophole that allowed for this dangerous exploit. This swift action not only mitigated the immediate threat but also reinforced the importance of timely updates and security best practices.
Lessons Learned and Moving Forward
The Haystack vulnerability serves as a valuable lesson for both developers and cybersecurity professionals. It highlights the critical need for thorough security reviews and audits, especially when dealing with tools and frameworks that process user-generated content. Here are a few key takeaways:
- Always validate and sanitize user inputs, particularly when using templating engines like Jinja2. This helps prevent injection attacks, including RCE.
- Stay up-to-date with the latest versions of software and frameworks. Vulnerabilities can often be patched in subsequent updates, as seen with Haystack’s quick release of version 2.3.1.
- Applications should operate with the minimum level of access necessary. This reduces the potential damage in the event of a security breach.
- Regular security audits, penetration testing, and code reviews are essential. They help identify vulnerabilities before malicious actors can exploit them.
In conclusion, the incident with Haystack and Jinja2 templates is a reminder that in cybersecurity, complacency can be costly. It underscores the importance of proactive security measures and the need for a continuous commitment to safeguarding system





