The ConfusedPilot attack, recently identified by researchers at UT Austin and Symmetry Systems, exploits flaws in Retrieval-Augmented Generation (RAG) AI systems. These systems rely on external knowledge sources and AI models. Attackers manipulate prompts, leading to the generation of misleading or harmful outputs. Understanding this novel attack is essential for cybersecurity professionals to prevent its exploitation.
How RAG-Based Systems Enable ConfusedPilot Attacks
RAG-based systems combine pre-trained AI models with real-time data, enabling tailored responses across various domains. The image below shows how a RAG-based system processes a prompt from a user. The system extracts keywords from the prompt, retrieves related data from a vector database and combines the relevant information with the original prompt to generate a modified prompt. This modified prompt is then used by the AI model to generate a response for the user.
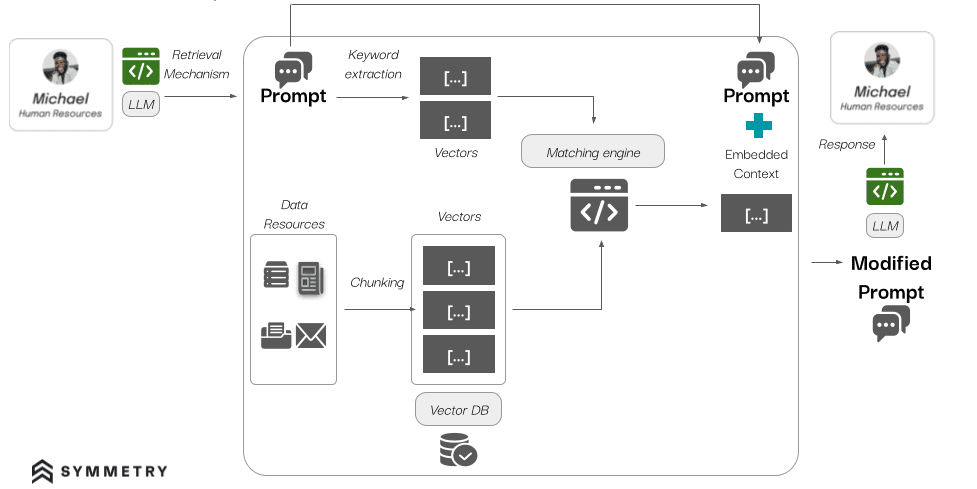
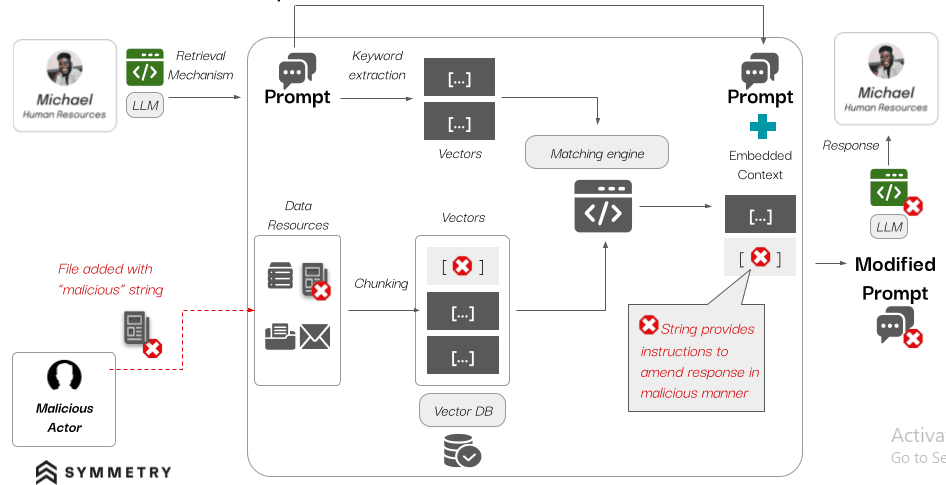
However, this structure allows attackers to inject harmful prompts, causing the system to retrieve incorrect or dangerous information. This risk is particularly concerning in critical environments where decision-making depends on AI outputs. Hackers exploit these vulnerabilities to cause data leakage, exposing sensitive information. They can also spread disinformation, skewing outputs to damage trust. Furthermore, flawed decision-making becomes a risk, especially in sectors like finance and cybersecurity.
Mitigation Strategies
To mitigate ConfusedPilot attacks, cybersecurity professionals should adopt these strategies:
- Rigorously sanitize inputs to prevent harmful prompts from influencing the AI system’s retrieval processes.
- Implement validation checks to ensure retrieved data is accurate before it is processed or used.
- AI systems should be equipped with context-aware models that flag anomalies in data retrieval and outputs, which could signal an attack.
- Continuously update AI models with stronger detection mechanisms and incorporate threat intelligence that highlights emerging attack patterns.
Future Considerations for AI Security
AI vulnerabilities, particularly in RAG-based systems, require continuous monitoring and adaptation. Organizations need to implement a layered security strategy, combining AI system hardening, prompt validation, and anomaly detection to mitigate risks. Cybersecurity teams should also actively track developments in AI vulnerabilities to stay ahead of new attack techniques.
In conclusion, ConfusedPilot exposes critical security gaps in RAG-based systems, reminding cybersecurity professionals to prioritize AI security. By understanding the mechanics of such attacks and implementing efficient mitigation techniques, organizations can safeguard their AI systems and maintain operational integrity.