Cybercriminals are now targeting Facebook users with fake AI editor ads that install password-stealing malware. These scams exploit the popularity of AI tools by luring users into downloading malicious software disguised as legitimate applications. Here’s a breakdown of how these attacks work and what cybersecurity professionals can do to protect users.
Analysis Of The Attack
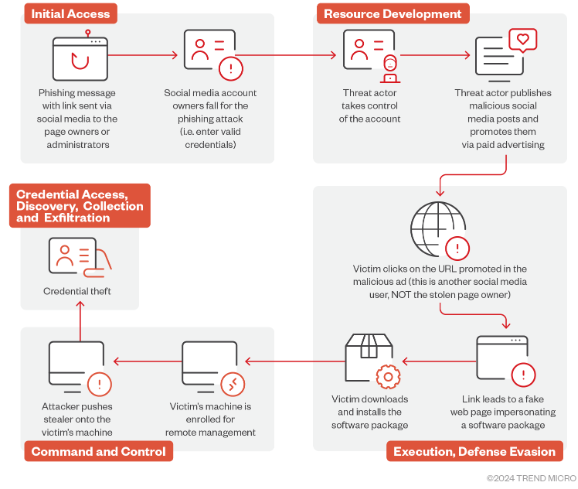
It all starts with phishing messages sent to Facebook page owners or administrators. These messages look like alerts from Facebook, urging users to click on a link to protect their accounts. The links lead to fake account protection pages that steal login credentials.
Once the attackers have the login credentials, they hijack the victims’ Facebook accounts. They use these accounts to post malicious ads promoting AI photo editing tools that appear legitimate.
When users click on these ads, they are redirected to websites that look like they belong to real AI tools. These fake websites prompt users to download a software package, which installs Lumma Stealer malware instead of delivering AI tools.
Lumma Stealer silently infiltrates a victim’s system, extracting sensitive information such as login credentials, cryptocurrency wallet files, browser data, and password manager databases. This stolen data is then sold to other cybercriminals or used to compromise victims’ online accounts and steal funds.
Protecting Against These Threats
- Adding MFA to all social media accounts provides an extra layer of security. Even if login credentials are stolen, MFA makes it harder for attackers to gain unauthorized access.
- Regularly educating users on recognizing phishing attempts can significantly reduce the risk. Users should be wary of unexpected messages and verify the legitimacy of links before clicking .
- Encourage users to double-check the URLs of sites they visit, especially those asking for personal information. Legitimate services can usually be accessed directly through trusted domains rather than through links in emails or ads.
- Implement systems to monitor for unusual account activities. Early detection and swift response can mitigate the impact of account hijacking. Be prepared with a response plan to address potential breaches quickly.
Conclusion
Cybercriminals have long used Facebook ads for attacks, but now they’re ramping up with fake AI editor ads. The use of fake AI editor ads on Facebook shows how attackers blend social engineering, account hijacking, and malware to create sophisticated scams. Hence, there’s a need to learn how these scams work and build tougher shields to protect users from them. The threat is getting bigger, so everyone needs to stay extra alert.
As we embrace new technologies, let’s also sharpen our security practices to keep one step ahead of those who would misuse them.





