Cybercriminals are always on the lookout for the next big opportunity to launch attacks. The latest target? Sora, OpenAI’s highly anticipated AI model. Cybercriminals have cleverly taken advantage of anticipation surrounding Sora AI, using it to spread malware through well-crafted phishing campaigns. In this article, we’ll break down the tactics and techniques these attackers are using and steps forward.
OpenAI’s Sora AI, with all of its promising capabilities, has gathered a lot of interest in the tech community. But while everyone’s focused on the possibilities, cybercriminals have seized the moment. They are launching phishing campaigns aimed at users eager to explore anything Sora-related. These scams actively leverage social engineering, tricking users into downloading what appears to be legitimate software connected to Sora AI through fake websites and compromised social media accounts.
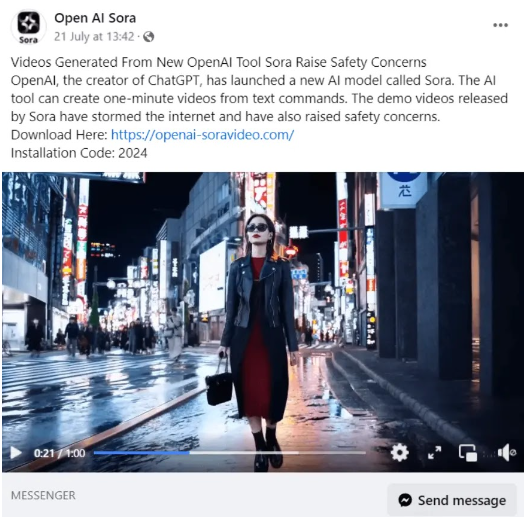
These fake websites are designed to look almost identical to real OpenAI platforms, luring users into thinking they’re getting early access or beta versions of Sora AI applications. Some of the phishing domains making the rounds are:
- hxxps://sora-openai-generation[.]com
- hxxps://sorics-ai[.]web.app
- hxxps://opensora-ai.web[.]app
- hxxps://sora-6b494[.]web.app
- hxxps://soraai-pro-kit[.]web.app
- hxxps://openai-soravideo[.]com
- hxxps://opensora[.]info
Furthermore, these sites promise features like text-to-video conversion, a much-anticipated Sora AI capability. But instead of delivering these, they deliver malware, including information stealers and cryptocurrency miners.
The malware distributed through these phishing campaigns comes in various forms, with attackers employing diverse techniques to stay undetected and maximize damage. Among the threats identified are Braodo Stealer, which is designed to steal sensitive information like login credentials and browser cookies, transmitting them to the attackers’ command and control (C2) servers.
Another set of malware, XMRig and lolMiner. They are cryptocurrency miners that covertly take over the victim’s computer, using its resources to mine cryptocurrency, significantly slowing down the system and increase energy consumption.
Additionally, some users download files containing PyInstaller executables with obfuscated Python scripts. These scripts, often protected by tools like PyArmor, execute additional malicious payloads, deepening the system compromise.
Social Engineering at Its Best (or Worst)
What makes this campaign particularly dangerous is the sophisticated social engineering used to spread the phishing links. Cybercriminals have managed to take control of popular social media accounts with large followings, using them to share links to malicious sites. These accounts look legit, which helps the phishing campaigns reach a wider audience, making it more likely that people will fall for the scam.
Given how advanced these attacks are, it’s important to be proactive in defending against them. Here are some steps you can take:
- Firstly, regularly inform users about the latest phishing tactics and remind them to only download software from official sources. Make sure they know that legitimate Sora AI downloads will only come from OpenAI’s official channels.
- Additionally, keep an eye on social media for compromised accounts that are spreading phishing links. Readily report and take down these accounts quickly.





