CVE-2024-45187, a vulnerability in the Mage AI framework, reveals severe concerns in session and privilege management, thereby presenting a risk of remote code execution. Identified by JFrog’s renowned Security Research Team in August 2024, this flaw, with a CVSS score of 7.1, allows attackers to execute arbitrary commands remotely on Mage AI’s terminal server. Exploiting improper session terminations, unauthorized users can retain access and elevate their privileges even after account deletion. This creates a window for severe security breaches, including full system compromise and data exfiltration, if not addressed immediately.
In a previous analysis, a path traversal vulnerability in Mage AI was observed, exposing sensitive data to unauthorized access. Building on this, recent findings now reveal an even more critical flaw.
The flaw comes from improper session management in Mage AI, where deleted guest accounts remain active with administrative privileges. This oversight grants attackers access to the terminal server, enabling them to execute arbitrary commands. As a result, attackers can compromise system integrity, manipulate configurations, and deploy malicious software, jeopardizing both system control and data security.
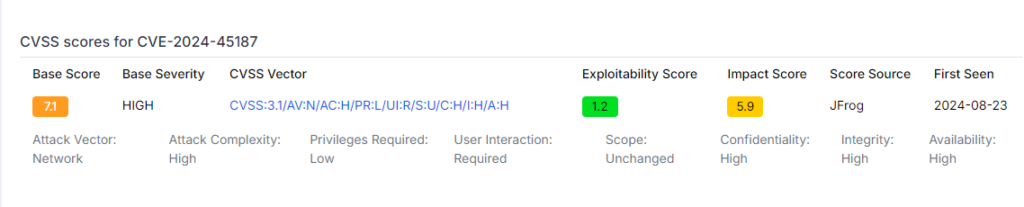
Classified under CWE-266 (Incorrect Privilege Assignment), the flaw reveals deeper issues in how the platform manages user privileges. Although no proof-of-concept (PoC) exploits have surfaced yet, experts emphasize the urgency of addressing this issue before attackers exploit it. Organizations using Mage AI in production face significant threats from CVE-2024-45187. Attackers could gain control of AI systems, disrupt operations, and steal sensitive data.
Consequences for AI Systems
Attackers could manipulate models or training data, leading to inaccurate results and damaging business outcomes. They could also deploy adversarial attacks, sabotaging AI operations and undermining system protections. The threat of data theft, particularly of sensitive AI training data, could have long-term repercussions for affected organizations.
Furthermore, the risk of remote code execution significantly raises concerns about supply chain attacks, especially in environments where AI systems depend on shared infrastructures and third-party services. An attacker could insert malicious code, which would propagate across interconnected systems, posing additional threats to broader AI infrastructure.
Mitigation Strategies
Although Mage AI has yet to release a patch, organizations can take immediate steps to mitigate the risks:
- Immediately end all sessions when a user account is deleted to prevent unauthorized access.
- Continuously audit user privileges and system access logs. This helps identify anomalies, such as deleted users who still appear active.
- Enforcing network segmentation will restrict access to Mage AI’s terminal server. Applying the principle of least privilege will reduce the risk of exploitation.
- WAFs can monitor and filter traffic between users and the Mage AI server. These firewalls will block suspicious or malicious requests, adding an extra layer of protection.
- Be on the lookout for security advisories from Mage AI. Apply patches as soon as they are available to minimize exposure to known vulnerabilities.
Conclusion
The discovery of CVE-2024-45187 emphasizes the importance of securing AI-driven platforms. As organizations increasingly rely on AI systems, the attack surface grows, making them attractive targets for cybercriminals. Addressing session management and privilege assignment issues proactively is crucial to safeguarding these systems.
Organizations must adopt a comprehensive security strategy that includes regular audits, real-time monitoring, and timely patching.





