Researchers have discovered a recent vulnerability CVE-2024-45189 in Mage AI, a data pipeline tool for transforming and integrating data. The vulnerability comes from a path traversal flaw in the “Git Content” request, that allows attackers with the “Viewer” role to remotely leak arbitrary files from the Mage AI server. Researchers published the flaw on August 23, 2024. Additionally, It is categorized as a high-confidentiality threat because of it’s potential exposure of sensitive information without requiring user interaction.
Technical Details
This vulnerability can be exploited with low privileges, requiring only access to a “Viewer” account on the Mage AI platform. Attackers can execute a path traversal attack by manipulating file paths to access restricted files. The path traversal occurs in the processing of “Git Content” requests, which do not sufficiently validate or sanitize user input. This allows attackers to access files outside the intended directories on the server, leading to data leakage.
One of the key factors that makes CVE-2024-45189 particularly dangerous is the absence of user interaction in the exploitation process. Attackers can carry out this exploit remotely, without needing to compromise additional accounts or escalate privileges. The vulnerability impacts versions of Mage AI up to v0.9.73, and as of now, there are no patches available.
The primary risk associated with CVE-2024-45189 is the exposure of sensitive data, which could include system configurations, private keys, or other critical information stored on the server. This vulnerability does not directly allow for data modification or service disruption. However, the confidentiality impact is high, and unauthorized access to critical files could lead to further compromise within an organization.
The vulnerability’s CVSS 3.1 vector is defined as:
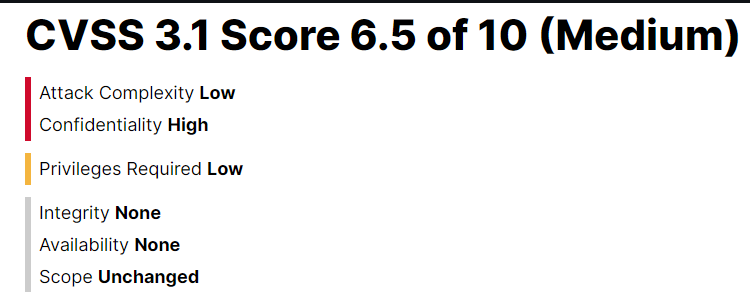
This shows that attackers can easily perform the attack over a network without physical access or user involvement.
Mitigation and Recommendations
Mage AI have not released an official patch yet. However, organizations can take several steps to mitigate the risks associated with
- Limit access to users who need it, and review all permissions associated with the Viewer role. Ensure that users with this role do not have access to critical server functions or sensitive files.
- Implement logging and monitoring mechanisms to detect any unusual requests or activities that might indicate an attempted path traversal exploit.
- Limit exposure of Mage AI servers to external networks, particularly for accounts with low-privilege roles such as “Viewer.”
- Conduct periodic reviews of system configurations and user access controls to identify and close any potential security gaps.
In conclusion, this vulnerability reminds us that attackers can leverage even seemingly low-privilege accounts in high-impact attacks when vulnerabilities stay unpatched. Furthermore, organizations can reduce the risk of data exposure by proactively restricting access, monitoring activity, and applying efficient security practices until an official patch is released.





