CVE-2024-32881 is a critical security vulnerability that was discovered in Danswer. Companies use Danswer, an AI assistant, to connect with internal documents, applications, and personnel. This vulnerability allows unauthorized access to Slack Bot Tokens, thereby, enabling an attacker to steal or modify these tokens, potentially leading to a complete compromise of internal Slack communications.
Technical Details
- Vulnerability ID: CVE-2024-32881
- CVSS Score: 9.8 (Critical)
- Affected Software: Danswer versions prior to 3.63
- Patch Available: Version 3.63
Description
The vulnerability in Danswer is as a result of improper authorization methods in managing Slack Bot Tokens. Specifically, the flaw allows attackers with network access to the Danswer system to:
- Retrieve existing Slack Bot Tokens.
- Update Slack Bot Tokens with arbitrary values.
These actions do not require authentication, which makes it easy for an attacker to gain unauthorized access to a company’s internal Slack environment.
CVSS Vector
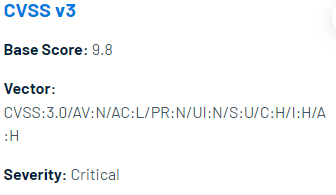
- Attack Vector (AV): Network (N): The vulnerability can be exploited remotely without local access to the system.
- Attack Complexity (AC): Low (L): Exploiting the vulnerability is relatively straightforward and doesn’t require advanced skills or resources.
- Privileges Required (PR): None (N): The attacker doesn’t need any privileges to exploit the vulnerability.
- User Interaction (UI): None (N): There’s no need for user interaction to exploit the vulnerability.
- Scope (S): Unchanged (U): Successful exploitation of the vulnerability doesn’t change the scope of the attack.
- Confidentiality (C): High (H): If exploited, the vulnerability could result in the disclosure of sensitive information.
- Integrity (I): High (H): The integrity of data could be compromised if the vulnerability is exploited, potentially allowing unauthorized modification.
- Availability (A): High (H): The availability of the system or service could be severely impacted, possibly leading to denial of service or other disruptions.
Exploit Details
The exploitation of this vulnerability is straightforward and does not require special privileges or user interaction, as seen in the attack vector above. Consequently, an attacker can perform the following actions using basic curl commands:
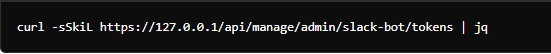
- Retrieve Slack Bot Tokens:
- Set New Slack Bot Tokens:
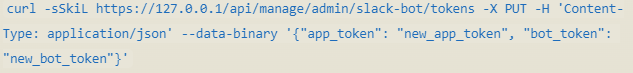
These commands exploit the vulnerability by sending requests to the Danswer API endpoints responsible for managing Slack Bot Tokens.
Impact
The potential impact of CVE-2024-32881 is severe. By manipulating Slack Bot Tokens, an attacker can:
- Impersonate Slack bots to send or manipulate messages.
- Gain access to sensitive information within Slack channels.
- Execute unauthorized commands within Slack, leading to data breaches and further security risks.
This vulnerability effectively opens a backdoor into an organization’s internal communications, posing a significant threat to data security and integrity.
Mitigation
To mitigate this vulnerability, it is crucial to:
- Update Danswer: Firstly, immediately upgrade to version 3.63, where the issue has been patched.
- Review Slack Bot Configurations: Furthermore, ensure that existing Slack bot configurations are secure and have not been tampered with.
- Network Security: In addition, implement network security measures to monitor and restrict access to sensitive API endpoints.
Conclusion
CVE-2024-32881 represents a critical vulnerability that demands immediate attention from cybersecurity professionals. As a result, organizations using Danswer should prioritize updating to the latest version and rigorously review their internal security practices to prevent unauthorized access and potential breaches.
Finally, regular monitoring and stringent access controls can significantly mitigate the risks associated with such vulnerabilities.





