The Flowise platform from FlowiseAI Inc. has a critical vulnerability that makes versions 1.6.2 and lower vulnerable to remote code execution attacks. Furthermore, this major vulnerability, identified as CVE-2024-31621, is caused by inadequate input validation in the api/v1 component, which lets attackers inject malicious code by delivering scripts that have been carefully designed.
The Root Cause: Inadequate Input Sanitization
This vulnerability is mostly caused by the application’s improper sanitization of user input. Threat actors can submit carefully constructed scripts that can be run on the server because the api/v1 component does not have enough validation procedures. This vulnerability is categorized as “Improper Control of Generation of Code” (CWE-94). It is a group of vulnerabilities that have the potential to cause serious security breaches and arbitrary code execution.
Assessing the Severity: CVSS Scores Raise Alarm
The severity of CVE-2024-31621 is reflected in its alarmingly high Common Vulnerability Scoring System (CVSS) scores:
- CVSS v2 Score: 7.5 (High): This score indicates the potential for partial data disclosure, modification, and service disruption, exploitable remotely without specialized conditions or authentication requirements.
- CVSS v3 Score: 9.8 (Critical): The CVSS v3 score is considerably more critical. This, thereby, indicates the potential for a complete compromise of data availability, confidentiality, and integrity. It may be achieved remotely without the need for human engagement or credentials.
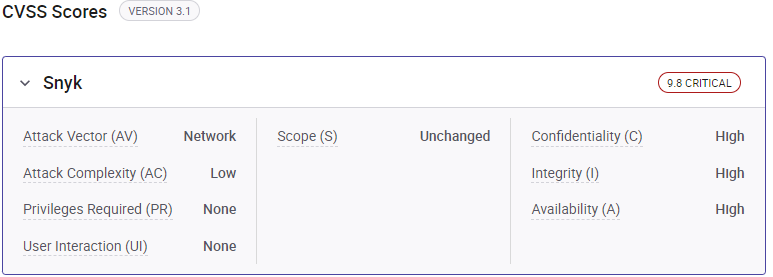
These ratings highlight how critical the vulnerability could be for the impacted systems. It tells how this could seriously compromise critical information, system integrity, and service availability.
Profound Impact and Mature Exploitation Potential
Successful exploitation of CVE-2024-31621 can have far-reaching consequences:
- Confidentiality Breach: Attackers can access and exfiltrate sensitive data, compromising the privacy and security of sensitive information.
- Data Integrity Violation: Malicious actors can modify data, inject false information, or tamper with system files. This undermines the reliability and trustworthiness of the affected systems.
- Denial of Service: Additionally, Attackers can disrupt services, potentially leading to a complete denial of service (DoS) attack. This rendering the affected systems unavailable to legitimate users.
Significantly, this vulnerability is regarded as “mature”. In terms of exploitability, this suggests that threat actors are probably aware of and actively employ solid exploitation techniques.
Proof of Concept Demonstrates Exploitation
An attacker can use this vulnerability by making a specially crafted request to the vulnerable endpoint. This is demonstrated by a Proof of Concept (PoC) that has been made public. For example:
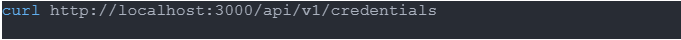
In order to replicate an attack vector, this command sends a malicious script to the api/v1 endpoint. This could allow for remote code execution on the targeted system
Mitigation and Remediation Strategies
As of the latest updates, no fixed version of Flowise has been released to address this vulnerability. Users are strongly advised to implement the following measures to mitigate the risk:
- Input Validation: Firstly, ensure proper sanitization and validation of all user inputs to prevent injection attacks.
- Access Controls: Restrict access to critical components and APIs to trusted users and applications only.
- Security Patches: Furthermore, regularly check for updates and apply security patches from FlowiseAI as soon as they are available.
- Monitoring and Detection: Lastly, Implement robust monitoring and detection mechanisms to identify and respond to suspicious activities promptly.





