Let’s face this, AI is transforming the world, and world leaders are sparing no cost in driving cutting-edge AI research and development. Every country wants to be the global powerhouse in AI advancement. It has led to a growing number of cyber espionage.
There are discussions on how attackers leverage on Artificial Intelligence to carry out cyber crimes. However, in this attack, threat actors used a combination of cyber attack techniques to target US AI Experts to steal vital information on Generative AI. These experts are associated with US companies, government agencies, and academia.
A threat actor known as UNK_SweetSpecter is responsible for targeting specific US experts in AI by utilizing a variant called SugarGh0st RAT. SugarGh0st RAT is a remote access trojan discovered by Cisco Talos in November 2013. UNK_SweetSpecter is associated with Chinese cybercrime activity. In this attack, the threat actors used an email to send an AI-themed phishing mail to their targets.
In this mail, they claimed to be a loyal user of an undisclosed tool. This user offered feedback on a problem they had discovered while using the app. They also attached a zip folder containing supposed feedback questions to be sent to technical support.
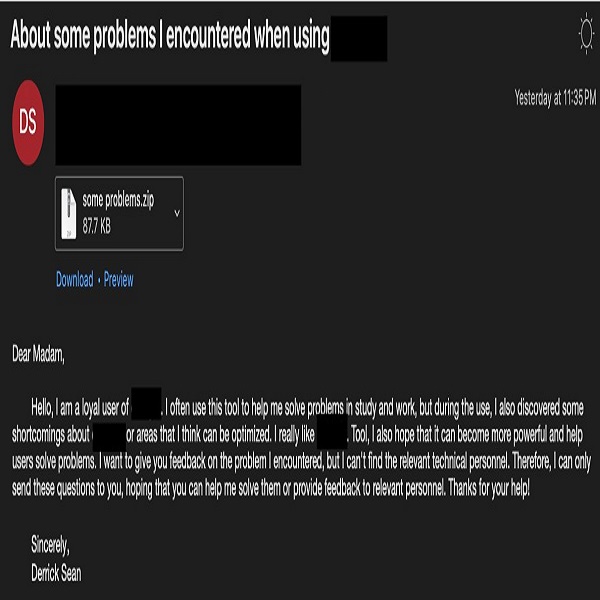
The main catch was in the Zip Archive. Proofpoint explains that after delivery, an attached zip file dropped a shortcut file. The shortcut file deployed a JavaScript dropper that contained a decoy document, an ActiveX tool for sideloading, and an encrypted binary, all encoded in base64. The infection chain ended with SugarGh0st deployed on the victim system and communicating with an attacker-controlled C2 server.
This attack process is similar to Infection Chain 2 reported by Cisco Talos when they discovered SugarGh0st RAT. The main functional differences between the two attacks were; a slightly modified registry key name, CTFM0N.exe, a reduced number of commands the SugarGh0st payload could run, and a different C2 server.
This attack seems to come from Chinese threat actors. With the constant battle for domination in AI between leading countries, the US government is taking measures to restrict Chinese access to generative AI technologies.
Research data must be kept secure. Experts should train to identify AI-themed phishing attacks to ensure that vital information is kept safe and does not fall into the wrong hands.